The difference between mobile management policies and technologies may come down to degrees of control, but deploying the wrong strategy can cost companies monetarily and kill employee morale.
When bring-your-own-device (BYOD) strategies first emerged several years ago, many corporations made device wiping a key goal; after all, the ability to delete data from an employee's smartphone or tablet appeared, on the surface, to be the best way to stop leaks or the misuse of sensitive information.
So, as employees, particularly senior-level workers, began demanding mobile devices for business use, IT often turned to either company-owned hardware or restrictive mobile device management (MDM) software.
Mobile Device Management
MDM allows IT to remotely enroll an employee or corporate-issued cell phone, tablet or other device and then track it, manage it and secure it through a profile specific to that employee and their tasks.
MDM lets a company provision and configure Wi-Fi access, install and manage enterprise apps such as email, and address any problems that arise on a device. It also allows IT to enforce device security, which can include locking out a device and wiping data if it's lost or an employee leaves a company.
![Mobile device management]()
GARTNER
(MDM policies typically involve having an employee sign an agreement allowing the company to delete data under those circumstances.)
One hitch in that scenario: Most employees are happier using their own mobile devices and don't like the idea of all their data, including personal photos and messages, being deleted.
Not only can MDM be overly invasive, it can also be wasteful. Many companies often over buy MDM software, expecting to use licenses for all employees. But they end up using licenses for a far smaller percentage of workers, according to research firm Gartner.
Mobile Application Management
There's a more targeted solution: mobile application management (MAM). This strategy locks down enterprise applications and the data associated with them -- not the devices themselves.
In short, MAM allows a company to control access to business applications and the content associated with them without controlling the entire physical device.
![Mobile device management]()
GARTNER
While corporate email is the most widely deployed form of MAM, employees may also be given secure access to a menu of applications, such as sales support, cloud storage or collaboration tools. Features such as copy and paste can also be limited, preventing employees from sharing corporate data with unapproved applications.
MAM allows IT to control just the access to and features of applications. That way, if an employee loses a device or leaves the company, the access to applications and business data can be removed from the smartphone, tablet or laptop, leaving personal data intact. MAM also allows applications to be remotely updated with new features and patches, making it easier to address new security threats quickly.
Compared to MDM and MAM, unified endpoint management (UEM) covers all hardware in an enterprise in one strategy.
Unified Endpoint Management
UEM allows IT to remotely provision, control and secure everything from cell phones, to tablets, laptops, desktops and now, Internet of Things (IoT) devices.
UEM can manage devices across a variety of platforms, theoretically, at least, making it easier to lockdown hardware and protect critical data. Although it is still a nascent IT strategy, and it lacks a full set of comprehensive tools, that situation is quickly changing.
For example, many of the basic application and system provisioning functions required for business laptops and PCs running Windows 10 can now be done through the OS's EMM control consoles, which are enabled by Microsoft's Intune protocol. That means organizations with more recent Windows PC deployments can use consolidated management tools and unified policy and configuration platforms via UEM.
![Mobile device management]()
GARTNER
UEM tools are rapidly becoming more advanced and can manage a variety of mobile devices and PCs with a single platform, said Phil Hockmuth, program director for Enterprise Mobility research at IDC.
"Some vendors are further along than others in terms of a full set of features and having the broadest set of devices supported," Hockmuth said. "Most vendors can manage Windows 10 equally well at a base level, as they all access a common set of APIs and management hooks in the OS for MDM-based management."
Vendors including VMware, MobileIron, BlackBerry and others are starting to add features to secure and manage Windows and other types of endpoints such as Chromebooks and IoT devices. Though adoption has been spotty, a lot of pilot programs are under way and the technologies are converging; that paves the way for companies preparing to dig into their UEM deployment plans, Hockmuth added.
In the same way UEM brings hardware under a single management strategy, enterprise mobility management (EMM) is aimed at all of the various software management tools under a single umbrella.
EMM defined
EMM is a comprehensive, hardware-agnostic method of remotely managing devices, including their configuration and the enterprise content generated on them, through MDM and MAM. EMM is all-encompassing; it can control access to corporate apps, internal websites and even the data silos associated with them.
![Mobile device management]()
GARTNER
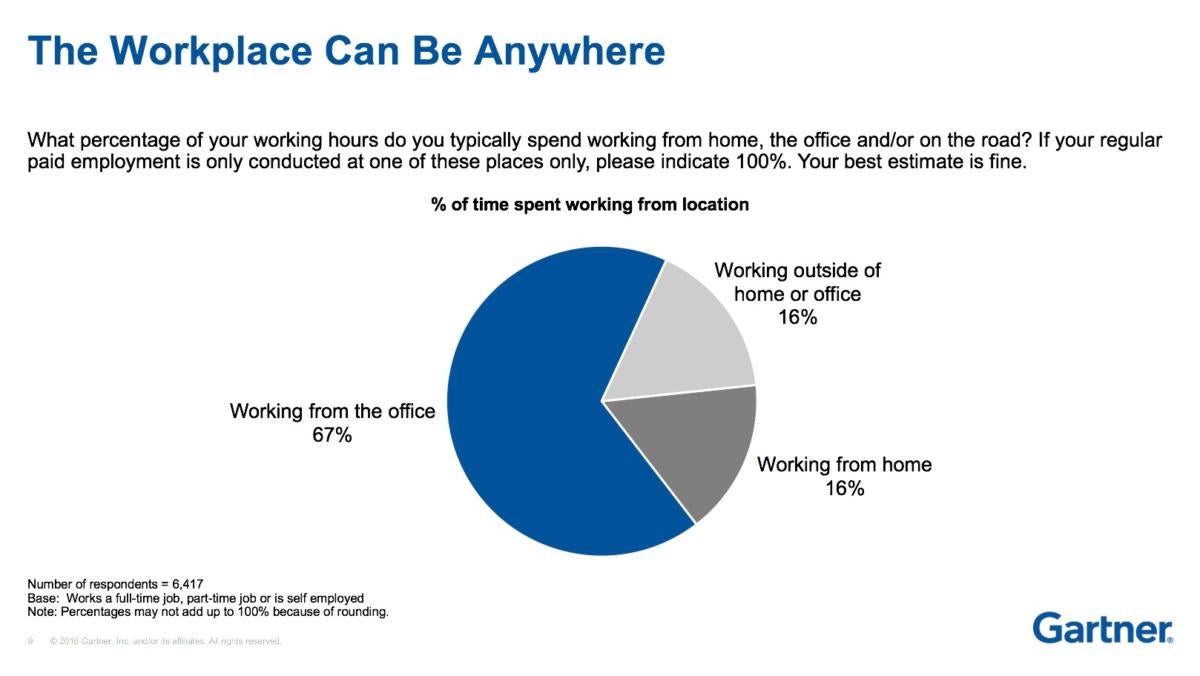
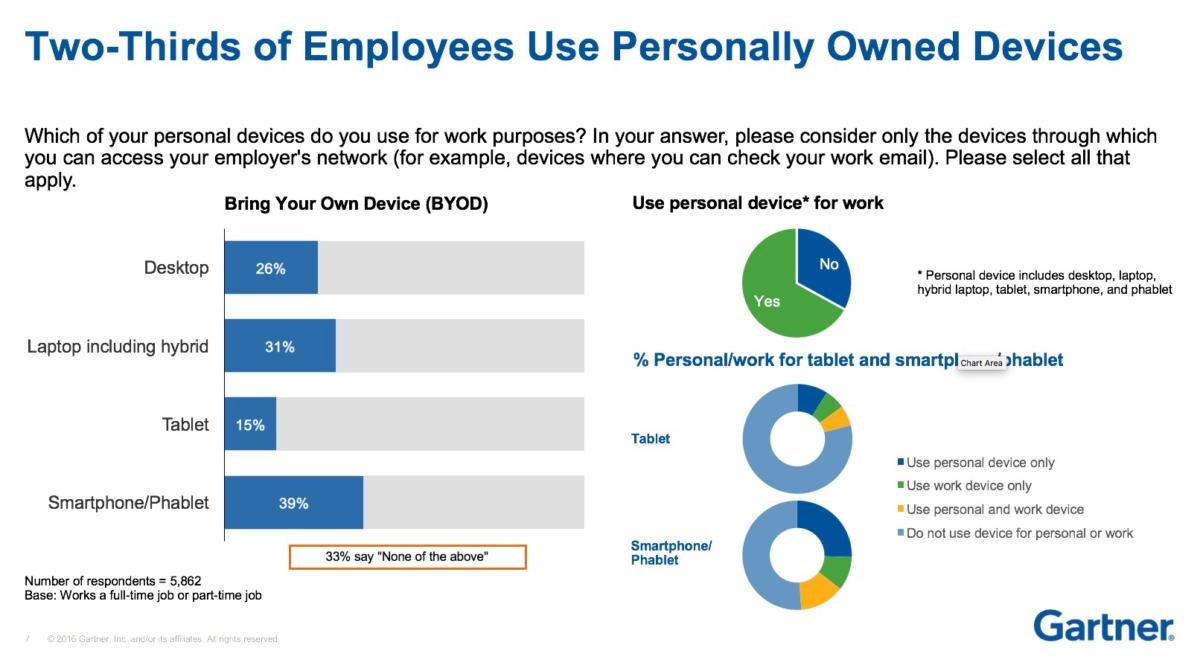
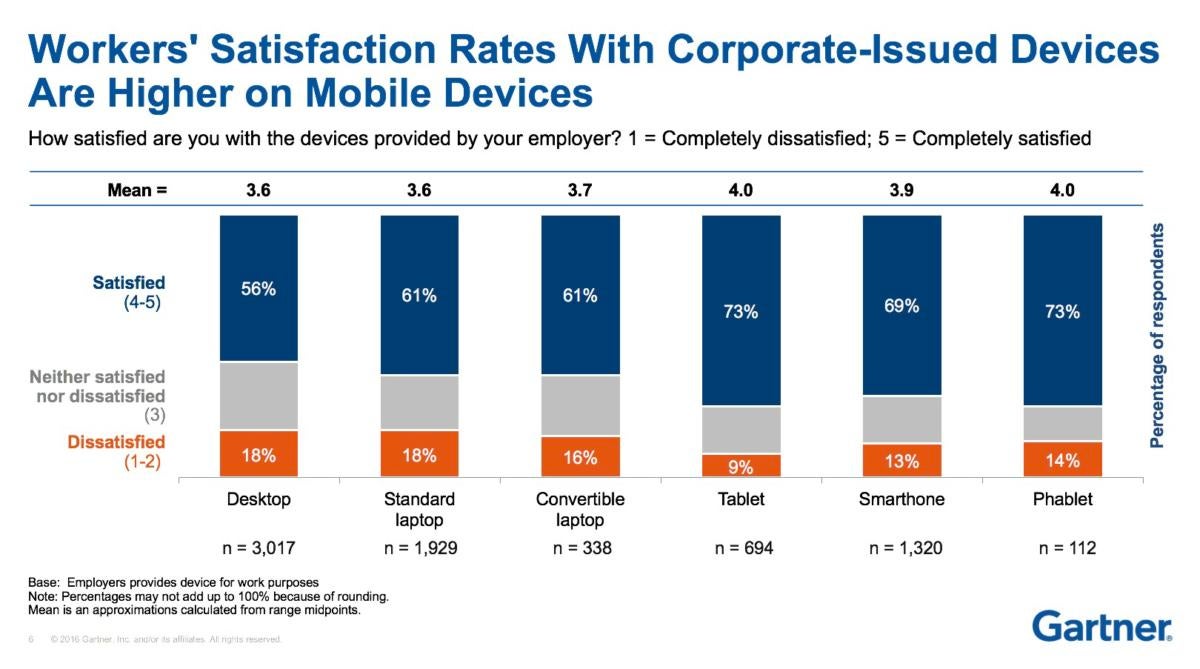
Even as mobile device adoption in the enterprise has grown over the past decade, it hasn't peaked yet, according to an analysis by Gartner.
A Gartner online survey done between June and August 2016 and involving 9,592 respondents in U.S., U.K. and Australia found:
- Eighty percent of employees consider PCs (desktops, notebooks and two-in-ones) as a main work device, regardless of whether they are corporate-issued or personally owned.
- Only 12% of employees receive corporate-issued tablets.
- The majority of smartphones used at work are personally owned, and only 22% of employees are given company-issued smartphones.
- Those who get corporate smartphones and tablets are more satisfied with the device than users of company-issued PCs.
- Tablets are the least-used device at work, as only 21% of respondents use them, including corporate-issued and personally owned ones.
- Two out of three workers use their own devices, including desktops, laptops, hybrid laptops, tablets, smartphones and phablets.